Content Form:APRJA 13 Mateus Domingos: Difference between revisions
No edit summary |
No edit summary |
||
| (49 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
'''Mateus Domingos ''' | |||
__NOTOC__ | __NOTOC__ | ||
<span class="running-header">Unstable Frequencies</span> | |||
= Unstable Frequencies = | = Unstable Frequencies = | ||
= A | = A Case for Small-scale Wifi Experimentation = | ||
== Abstract == | == Abstract == | ||
In this essay I describe an experimental wifi network ''sideBand'' which provided access to a simple message-board during the Content/Form workshop, held at Haus der Kulturen der Welt in January 2024. This is considered in relation to the collaborative infrastructure ''ServPub'' that was carefully assembled and maintained for the workshop. The production of the hardware and software required for the sideBand network is described with specific consideration of the types of memory and data storage systems that are utilised. The programming that provided message-board (and wider) functionality is also described. The conditions of this production along with the specific ways in which use of the network unfolds are considered in relation to Dunbar-Hester’s propagation and a Luddite framing, that includes sabotage and refusal. This is argued as producing other ways of understanding infrastructure and place, related to the feminist methodologies of ServPub. | In this essay I describe an experimental wifi network ''sideBand'' which provided access to a simple message-board during the ''Content/Form'' workshop, held at Haus der Kulturen der Welt in January 2024, as part of transmediale. This is considered in relation to the collaborative infrastructure ''ServPub'' that was carefully assembled and maintained for the workshop. The production of the hardware and software required for the sideBand network is described with specific consideration of the types of memory and data storage systems that are utilised. The programming that provided message-board (and wider) functionality is also described. The conditions of this production along with the specific ways in which use of the network unfolds are considered in relation to Dunbar-Hester’s propagation and a Luddite framing, that includes sabotage and refusal. This is argued as producing other ways of understanding infrastructure and place, related to the feminist methodologies of ServPub. | ||
== | <div class="page-break"></div> | ||
The ''Content/Form'' research workshop questioned of the ways in which research practices are "shared and reviewed, and the infrastructures through which | |||
== Introduction == | |||
The ''Content/Form'' research workshop questioned of the ways in which research practices are "shared and reviewed, and the infrastructures through which [they are] served." Participants gained access to the specially convened ServPub infrastructure, engaging with the self-managed server and the various software and memory systems provided.<ref>ServPub is inclusive of hardware, software and the broad constellation of people engaged in this careful practice. It is a collective of collectives, comprised of SysterServer, In-grid, Creative Crowd/Varia, Centre for the Study of the Networked Image at London South Bank University, UCL Slade Schoool of Art, and SHAPE at Aarhus University.</ref> Inviting space for a parallel imagination of these networks, I used wifi-enabled micro-controllers to introduce offline access points, serving a simple message board (referred to hereafter as sideBand). I argue that this intervention provokes a counter-knowledge of the internet and networking infrastructures. My intention was for sideBand to act as a shadow network to the primary shared space of ServPub, augmenting our interactions with the server and the collective writing processes. | |||
Networked data streams always function through protocological layers which perform different functions that in combination allow communication or transmission. They do so within a chain of binary data operating along a one-dimensional line. As Alexander Galloway describes: | Networked data streams always function through protocological layers which perform different functions that in combination allow communication or transmission. They do so within a chain of binary data operating along a one-dimensional line. As Alexander Galloway describes: | ||
| Line 25: | Line 27: | ||
Following the naming conventions of the newspaper and ''wiki4print'' (Berends, Browne), I’ll use the word ''editors'' to refer to users of the wiki4print platform, which includes the workshop participants, organisers and caretakers of the infrastructure. | Following the naming conventions of the newspaper and ''wiki4print'' (Berends, Browne), I’ll use the word ''editors'' to refer to users of the wiki4print platform, which includes the workshop participants, organisers and caretakers of the infrastructure. | ||
== | == Mapping == | ||
The ServPub infrastructure has been documented in depth by its participants in the newspaper, online, and within this journal. Based on the diagram by Mara Karagianni, I include a brief outline of the structure here in order to contextualise the observations I am drawing. This diagram also shows how the sideBand network occupies space alongside the ServPub network. | The ServPub infrastructure has been documented in depth by its participants in the newspaper, online, and within this journal. Based on the diagram by Mara Karagianni, I include a brief outline of the structure here in order to contextualise the observations I am drawing. This diagram also shows how the sideBand network occupies space alongside the ServPub network. | ||
[[File: | [[File:fig1-networkdiagram.jpg|thumb|480px|Figure 1: Network diagram (based on Karagianni).]] | ||
The diagram maps the modes of connection to the sideBand network, the ServPub organised wiki4print platform and common retrieval of websites. The editor is imagined as selecting a wifi network or service set identifier (SSID) to join at which point the paths of data diverge. In the organisation of this diagram, blocks closer to the top of the diagram are more likely visible to the editors. This visibility mostly aligns with opportunity for control over those blocks (e.g. through removing the power source). | The diagram maps the modes of connection to the sideBand network, the ServPub organised wiki4print platform and common retrieval of websites. The editor is imagined as selecting a wifi network or service set identifier (SSID) to join at which point the paths of data diverge. In the organisation of this diagram, blocks closer to the top of the diagram are more likely visible to the editors. This visibility mostly aligns with opportunity for control over those blocks (e.g. through removing the power source). | ||
| Line 38: | Line 40: | ||
A key distinction, which situates the following essay, is contained within the first step from editor device to the network. The ServPub setup was joined via the wifi provided by the workshop venue, and as such, not controlled by the participants. As the network included multiple servers in different locations, the data was making long international loops to reach back to the device that was in the room. Conversely the sideBand network was contained within the room, with data passing directly between the sideBand device and the editor device. | A key distinction, which situates the following essay, is contained within the first step from editor device to the network. The ServPub setup was joined via the wifi provided by the workshop venue, and as such, not controlled by the participants. As the network included multiple servers in different locations, the data was making long international loops to reach back to the device that was in the room. Conversely the sideBand network was contained within the room, with data passing directly between the sideBand device and the editor device. | ||
== | == Side Bands == | ||
This kind of networking performed by the sideBand, could perhaps be described as shadow-networking, borrowing the nomenclature from shadow libraries and the dark web. These practices challenge the permitted use of existing infrastructures. Their operation follows pirate principles (Sumi 13). The uses of sideBand that editors took most interest in was perhaps those that performed as elements of a shadow library structure. I am using the term sideBands to refer more specifically to a technical phenomenon, that relates to the relational quality of the networks. | This kind of networking performed by the sideBand, could perhaps be described as shadow-networking, borrowing the nomenclature from shadow libraries and the dark web. These practices challenge the permitted use of existing infrastructures. Their operation follows pirate principles (Sumi 13). The uses of sideBand that editors took most interest in was perhaps those that performed as elements of a shadow library structure. I am using the term sideBands to refer more specifically to a technical phenomenon, that relates to the relational quality of the networks. | ||
| Line 45: | Line 47: | ||
Rhyming with the side band phenomenon, the kind of networking explored with the sideBand exists within the affordances of protocol that collectively assemble into a functioning internet. A selective use and adaptation of parts of this framework generate a different system of transmission. It directly utilises a narrowing of frequencies and the ability to re-assemble transmissions. This occurs through the selective use of wifi channels and the local, social structure, or bodies, that are present with the devices. | Rhyming with the side band phenomenon, the kind of networking explored with the sideBand exists within the affordances of protocol that collectively assemble into a functioning internet. A selective use and adaptation of parts of this framework generate a different system of transmission. It directly utilises a narrowing of frequencies and the ability to re-assemble transmissions. This occurs through the selective use of wifi channels and the local, social structure, or bodies, that are present with the devices. | ||
It is in some respects an inversion of the ServPub model. Instead of creating a communal, distributed infrastructure, a looser proliferation of isolated networks is expected. This inherently limits the scope of the activity whilst surfacing a visibility of components and network paths. The hardware is built from comparatively few components, most of which are clearly visible. This affords an awareness of processes that relates to Christian Ulrik | It is in some respects an inversion of the ServPub model. Instead of creating a communal, distributed infrastructure, a looser proliferation of isolated networks is expected. This inherently limits the scope of the activity whilst surfacing a visibility of components and network paths. The hardware is built from comparatively few components, most of which are clearly visible. This affords an awareness of processes that relates to Christian Ulrik Andersen and Søren Bro Pold's framing of technology critique that combine "semantic processes of signification with machinic processes of signals." (14) | ||
There is also a link here to radio activism, as described by Christina Dunbar-Hester in her account of low power FM radio activism and the Prometheus Radio Project. Dunbar-Hester argues that these radio activists are "'propagators’ of technology." | There is also a link here to radio activism, as described by Christina Dunbar-Hester in her account of low power FM radio activism and the Prometheus Radio Project. Dunbar-Hester argues that these radio activists are "'propagators’ of technology." | ||
| Line 59: | Line 61: | ||
''Luddism'' in its original guise was resistant to changes rendered in the workplace, often embodied in the deployment of machinery that automated increasing stages of production processes. Its methods of refusal and sabotage attacked these machines, and it is commonplace to articulate a Luddite stance in regard to contemporary technologies, or as certain effects of their use become apparent. Despite its eventual suppression and failures, Luddism suggests techniques for organisation and collective action. The methods of resistance employed and reasons for it were not unique to Luddism, but rather appear as part of a tapestry of woven solidarities and movements that emerged from the specific conditions imposed on the population (Thompson). | ''Luddism'' in its original guise was resistant to changes rendered in the workplace, often embodied in the deployment of machinery that automated increasing stages of production processes. Its methods of refusal and sabotage attacked these machines, and it is commonplace to articulate a Luddite stance in regard to contemporary technologies, or as certain effects of their use become apparent. Despite its eventual suppression and failures, Luddism suggests techniques for organisation and collective action. The methods of resistance employed and reasons for it were not unique to Luddism, but rather appear as part of a tapestry of woven solidarities and movements that emerged from the specific conditions imposed on the population (Thompson). | ||
Dunbar-Hester is careful to distinguish propagators from 'mere' Luddites (Dunbar-Hester | Dunbar-Hester is careful to distinguish propagators from 'mere' Luddites (Dunbar-Hester 181). The radio activism she describes emerges more through uses of specific technologies and appeals to legal frameworks than a retreat from legal options and a destruction of machinery. I don’t quite draw such a distinction as the Luddite activities did include attempts at gaining certain protections through charters and the halting destruction of machinery could reflect a radical flank of a wider movement agitating against the imposed conditions (Malm 50). | ||
The sideBand provocation was suggestive of some of the Luddite strategies, if not also performing them in some minor ways. Including, forms of sabotage and refusal. Sabotage – or ''the withdrawal of efficiency'' (Flynn), is enacted through occupation of the network spaces with brittle replacements (sideBand micro-controllers). Refusal is understood through the call to "put down all machinery harmful to commonality" (Binfield 57). Recognising implicit harms to commonality in conventional computational technologies and networking infrastructure, the sideBand escapes (or limits exposure to) some aspects of the conventional networking infrastructure (which is essential to larger scale networking) as does Servpub. | The sideBand provocation was suggestive of some of the Luddite strategies, if not also performing them in some minor ways. Including, forms of sabotage and refusal. Sabotage – or ''the withdrawal of efficiency'' (Flynn), is enacted through occupation of the network spaces with brittle replacements (sideBand micro-controllers). Refusal is understood through the call to "put down all machinery harmful to commonality" (Binfield 57). Recognising implicit harms to commonality in conventional computational technologies and networking infrastructure, the sideBand escapes (or limits exposure to) some aspects of the conventional networking infrastructure (which is essential to larger scale networking) as does Servpub. | ||
| Line 65: | Line 67: | ||
Through the limited sideBand nodes, there is a potential that these processes of sabotage and refusal ''can'' be negotiated and performed, if only as a limited moment of reflection and critique within the small scale of the workshop. As networking complexity increases, the malleability of the systems for novice programmers is diminished. This isn't intended to argue for non-complexity in the infrastructures we attempt to build as communities. It is instead about a parallel point of access that supports propagation and provides waypoints to complexity. | Through the limited sideBand nodes, there is a potential that these processes of sabotage and refusal ''can'' be negotiated and performed, if only as a limited moment of reflection and critique within the small scale of the workshop. As networking complexity increases, the malleability of the systems for novice programmers is diminished. This isn't intended to argue for non-complexity in the infrastructures we attempt to build as communities. It is instead about a parallel point of access that supports propagation and provides waypoints to complexity. | ||
== | == Components == | ||
The ServPub network operated across a range of machines. Centrally it was using multiple Raspberry Pi's. In the same way that all commercially available computer systems should be challenged regarding their ecological impacts and ethical implications (Arboleda; Kara; Starosielski), the Raspberry Pi can be seen as a troubling device for communities engaged with anti-colonial and feminist protest. | The ServPub network operated across a range of machines. Centrally it was using multiple Raspberry Pi's. In the same way that all commercially available computer systems should be challenged regarding their ecological impacts and ethical implications (Arboleda; Kara; Starosielski), the Raspberry Pi can be seen as a troubling device for communities engaged with anti-colonial and feminist protest. | ||
| Line 72: | Line 74: | ||
The ESP8266 is produced by Chinese semiconductor firm, Espressif. They describe themselves as a world leading AIoT (Artificial Intelligence of Things) company and by late 2023 they had shipped over 1 billion chips (Espressif). They are well known for their ESP range of chips which feature networking components such as wifi. Their devices are designed to work with Espressif's own open-source SDKs as well as other alternatives, such as Arduino. As with Raspberry Pi, they are designed primarily for industrial use. The ESP chips have also been developed into so-called development boards. This places the chip within a printed circuit board that contains the necessary components to enable simple programming and operation, allowing inputs/outputs and USB connection. The model I am using is the ''D1 Mini'', originally designed by Lolin (based on a module by Ai-Thinker). As they became available in these hobbyist-friendly forms they were quickly adopted as a flexible part of IoT (Internet of Things) tinkering, despite initially having no English documentation (Benchoff). | The ESP8266 is produced by Chinese semiconductor firm, Espressif. They describe themselves as a world leading AIoT (Artificial Intelligence of Things) company and by late 2023 they had shipped over 1 billion chips (Espressif). They are well known for their ESP range of chips which feature networking components such as wifi. Their devices are designed to work with Espressif's own open-source SDKs as well as other alternatives, such as Arduino. As with Raspberry Pi, they are designed primarily for industrial use. The ESP chips have also been developed into so-called development boards. This places the chip within a printed circuit board that contains the necessary components to enable simple programming and operation, allowing inputs/outputs and USB connection. The model I am using is the ''D1 Mini'', originally designed by Lolin (based on a module by Ai-Thinker). As they became available in these hobbyist-friendly forms they were quickly adopted as a flexible part of IoT (Internet of Things) tinkering, despite initially having no English documentation (Benchoff). | ||
[[File: | [[File:Fig2-stack.jpg|thumb|480px|Figure 2: Diagram of some manufacturers at different stages of the development board production.]] | ||
The D1 Mini contains a handful of visible components. The antenna is a copper trace etched onto the board like a strange glyph. The intended use of the board is signed and performed by this as the length of the trace corresponds to antenna theory and is (with an adjustment for impedance) a quarter wavelength long (Pattnayak, Thanikachalam 4). Because the hardware is open sourced it allows hobbyists to experiment with the construction of these boards. This structure means that it is possible for hobbyists to design their own versions of these development boards and have them manufactured with relative ease (Feranec). This means that there are also many different companies producing these development boards, and that they continue to be readily available despite their limitations and superior later models. | The D1 Mini contains a handful of visible components. The antenna is a copper trace etched onto the board like a strange glyph. The intended use of the board is signed and performed by this as the length of the trace corresponds to antenna theory and is (with an adjustment for impedance) a quarter wavelength long (Pattnayak, Thanikachalam 4). Because the hardware is open sourced it allows hobbyists to experiment with the construction of these boards. This structure means that it is possible for hobbyists to design their own versions of these development boards and have them manufactured with relative ease (Feranec). This means that there are also many different companies producing these development boards, and that they continue to be readily available despite their limitations and superior later models. | ||
[[File: | [[File:Fig3-block-diagram.jpg|thumb|480px|Figure 3: ESP8266 Block diagram (based on Espressif).]] | ||
To program the board I have been using Arduino, "an open-source electronics platform based on easy-to-use hardware and software." (Arduino) It is a popular choice for hobbyists to experiment with electronics, often utilising sensors and other components. The integrated development environment (IDE) shares a lineage with experimental artistic coding as it built on ''Wiring'' (Barragán) which the creators of ''Processing'', Casey Reas and Ben Fry describe as "an electronics version of Processing that used our programming environment and was patterned after the Processing syntax" (Shiffman). It's relevant to note as well, that Reas and Fry also express their excitement at the "iteration and growth of this community" and cite the earlier software and projects that informed Processing. | To program the board I have been using Arduino, "an open-source electronics platform based on easy-to-use hardware and software." ("What Is Arduino?") It is a popular choice for hobbyists to experiment with electronics, often utilising sensors and other components. The integrated development environment (IDE) shares a lineage with experimental artistic coding as it built on ''Wiring'' (Barragán) which the creators of ''Processing'', Casey Reas and Ben Fry describe as "an electronics version of Processing that used our programming environment and was patterned after the Processing syntax" (Shiffman). It's relevant to note as well, that Reas and Fry also express their excitement at the "iteration and growth of this community" and cite the earlier software and projects that informed Processing. | ||
== Message | == Message Board == | ||
The sideBand locally hosts a simple message board website. It is a small page of HTML that assembles itself each time it is requested, to include any new data submitted by the editors. It makes use of a handful of basic HTML elements with styling performed inline. The more complex element is the form, which provides the functionality for editors to post messages. The messages are stored as variables that pass through the Arduino code and are able to act in parts of the program other than the displayed HTML. Despite being messy and inefficient, the code for this program is quite accessible for editors with little coding experience. Much of the functionality of the sideBand server is contained and performed within libraries that are part of the IDE. In the process of programming, we can call on these libraries and use certain functions with the expectation that they will continue to perform expected tasks (such as handle new editors joining the SSID). | The sideBand locally hosts a simple message board website. It is a small page of HTML that assembles itself each time it is requested, to include any new data submitted by the editors. It makes use of a handful of basic HTML elements with styling performed inline. The more complex element is the form, which provides the functionality for editors to post messages. The messages are stored as variables that pass through the Arduino code and are able to act in parts of the program other than the displayed HTML. Despite being messy and inefficient, the code for this program is quite accessible for editors with little coding experience. Much of the functionality of the sideBand server is contained and performed within libraries that are part of the IDE. In the process of programming, we can call on these libraries and use certain functions with the expectation that they will continue to perform expected tasks (such as handle new editors joining the SSID). | ||
[[File:Image3.png|thumb|480px| | <!-- | ||
[[File:Image3.png|thumb|480px|Figures 4]] | |||
[[File:Image4.png|thumb|480px | [[File:Image4.png|thumb|5|480px]] | ||
[[File:Image5.png|thumb|480px| | [[File:Image5.png|thumb|6|480px]] | ||
--> | |||
{| class="wikitable sideBand" | |||
|- | |||
| [[File:Image3.png|thumb|180px|Figures 4, 5, 6]] || [[File:Image4.png|thumb| |180px]] || [[File:Image5.png|thumb| |180px]] | |||
|} | |||
Foregoing some of the checks that might be made as standard practice if deploying a form online primarily to avoid code injection attacks, minimal checks are here performed on the validity of submitted data. This introduces an unstable zone, where editors have increased agency over the functionality of the message board. They could, for example, submit HTML markup to alter the display of the posts. This is also a vector through which the editors could disable the board if they chose to. This brittle state can be both useful and limiting. | Foregoing some of the checks that might be made as standard practice if deploying a form online primarily to avoid code injection attacks, minimal checks are here performed on the validity of submitted data. This introduces an unstable zone, where editors have increased agency over the functionality of the message board. They could, for example, submit HTML markup to alter the display of the posts. This is also a vector through which the editors could disable the board if they chose to. This brittle state can be both useful and limiting. | ||
== Memories == | |||
When using computers, we are interacting with machines that manipulate data and instructions following established architectures, with differing affordances. These machines are usually based on the Von Neumann architecture, in which the "data and instructions are both stored in primary storage" (BBC). An alternative to this is the Harvard architecture, meaning that data and instructions are stored separately. This architecture remains common in microcontrollers where the limited instruction and data memory make it suitable (Fouilloux). This provides an interesting point of difference in the fundamental interaction with these devices and general processes of computation. | When using computers, we are interacting with machines that manipulate data and instructions following established architectures, with differing affordances. These machines are usually based on the Von Neumann architecture, in which the "data and instructions are both stored in primary storage" (BBC). An alternative to this is the Harvard architecture, meaning that data and instructions are stored separately. This architecture remains common in microcontrollers where the limited instruction and data memory make it suitable (Fouilloux). This provides an interesting point of difference in the fundamental interaction with these devices and general processes of computation. | ||
| Line 97: | Line 106: | ||
to read the code visually using advanced microscopy techniques (Courbon, Skorobogatov, Woods).<ref> The process of deciphering programming from photography of chips is commonly part of reverse-engineering efforts aimed at proprietary and/or old hardware (Ilmer; Shirriff).</ref> | to read the code visually using advanced microscopy techniques (Courbon, Skorobogatov, Woods).<ref> The process of deciphering programming from photography of chips is commonly part of reverse-engineering efforts aimed at proprietary and/or old hardware (Ilmer; Shirriff).</ref> | ||
[[File:Fig4 flash. | [[File:Fig4-flash.jpg|thumb|480px|Figure 7: Flash Memory diagram (based on AnandTech).]] | ||
Accessing the sideBand network would in most cases force a user to disconnect from other networks | Accessing the sideBand network would in most cases force a user to disconnect from other networks since the usual operation of phones or laptops only allows for a connection to one wifi network at a time to avoid routing conflicts. On some devices this process prompts a warning to the editor that they will not be able to connect to the internet. In the process of connecting to a new network some devices will try to ping a service, in order to receive a response confirming they are online. The response generated when connected to the sideBand network is unsuccessful and so triggers the warning. The device presents this as something you shouldn't do and circumventing it usually takes a few more steps to assure the device that you do wish to connect to this offline network. This hints at the levels of invisible communication our devices have with centralised platforms throughout their use. | ||
If the sideBand microcontroller is reset or encounters an error, the data posted to the message log is not saved. Drawing on Eugene Thacker's assertion that "the moment of disconnectivity is the moment when protocol most forcefully displays its political character" (Thacker xvi) we can identify this as a crucial part in our understanding of the political possibilities that the sideBand represents. The use of the network is collectively understood to be temporary and subject to either chance failure or forced failure (as through code injection, or switching off the power supply). This necessarily shapes what a community might decide to share there or not. Methods of saving the log could also be enacted if the editors wished. Once the page has loaded to their device they could save the page locally or make screenshots at any time. | If the sideBand microcontroller is reset or encounters an error, the data posted to the message log is not saved. Drawing on Eugene Thacker's assertion that "the moment of disconnectivity is the moment when protocol most forcefully displays its political character" (Thacker xvi) we can identify this as a crucial part in our understanding of the political possibilities that the sideBand represents. The use of the network is collectively understood to be temporary and subject to either chance failure or forced failure (as through code injection, or switching off the power supply). This necessarily shapes what a community might decide to share there or not. Methods of saving the log could also be enacted if the editors wished. Once the page has loaded to their device they could save the page locally or make screenshots at any time. | ||
Increasing usage of the sideBand also increases the likelihood of it failing. The code was written in such a way that it would soon reach the limits of its memory and require resetting. This was indicated in the website interface with a counter that showed current available memory. The sideBand is brittle and limited. For any sustained use it requires a careful, deliberate kind of engagement; with an expanded possibility to slow, pause or preserve the data that emerges. | Increasing usage of the sideBand also increases the likelihood of it failing. The code was written in such a way that it would soon reach the limits of its memory and require resetting. This was indicated in the website interface with a counter that showed current available memory. The sideBand is brittle and limited. For any sustained use it requires a careful, deliberate kind of engagement; with an expanded possibility to slow, pause or preserve the data that emerges. | ||
== Admission == | |||
The use of the sideBand starts from a collective expectation of its limits as described above. It is important that they were introduced to the group in this way to be clear in the way that the network was lacking features that might be expected. Admission to the space requires knowledge to be shared between peers. In this sharing of the password the group of editors becomes possible. Bypassing a usual layer of internet browsing, the message board website is reached at an IP address instead of a domain name. | The use of the sideBand starts from a collective expectation of its limits as described above. It is important that they were introduced to the group in this way to be clear in the way that the network was lacking features that might be expected. Admission to the space requires knowledge to be shared between peers. In this sharing of the password the group of editors becomes possible. Bypassing a usual layer of internet browsing, the message board website is reached at an IP address instead of a domain name. | ||
Beyond the option of removing the sideBand power supply there are no moderation tools or policies enforced by the software. The acceptable behaviours of a group of people working together, with computers that might usually be ceded to established hardware and software limitations or a coded range of possibilities remain negotiable using other channels within the room, such as voice, a handwritten note, or list of rules taped to a wall. | Beyond the option of removing the sideBand power supply there are no moderation tools or policies enforced by the software. The acceptable behaviours of a group of people working together, with computers that might usually be ceded to established hardware and software limitations or a coded range of possibilities remain negotiable using other channels within the room, such as voice, a handwritten note, or list of rules taped to a wall. | ||
This process of admission and group formation echoes the use of oaths and passwords within many organisations, covert or not. The Luddites, for example, called the initiation of the oath, "the tying in". It was deemed at that time a transgressive act, and punishable by execution or transportation (Ludd). These processes of course rely on the bonds of trust and honesty between the participants, and produce an interdependence For the Luddites this was frequently undermined by the infiltration of government spies. The uses of the sideBand described here do not necessarily produce outcomes that require careful sensitivity as to the process of admission. However, it does form a space that is potentially subject to legal ramifications both in the content posted to it, and the locations of its deployment. An example of this could have been political organising, particularly around calls for "boycotting, divesting and sanctioning The Cloud Regime" (Counter Cloud Action Day), which were present at the festival and subject to differing levels of censorship (Anti-Colonial Tech Panel), along with the anti-extremism protest that took place metres from the festival venue (Rinke and Steitz). | This process of admission and group formation echoes the use of oaths and passwords within many organisations, covert or not. The Luddites, for example, called the initiation of the oath, "the tying in". It was deemed at that time a transgressive act, and punishable by execution or transportation (Ludd). These processes of course rely on the bonds of trust and honesty between the participants, and produce an interdependence For the Luddites this was frequently undermined by the infiltration of government spies. The uses of the sideBand described here do not necessarily produce outcomes that require careful sensitivity as to the process of admission. However, it does form a space that is potentially subject to legal ramifications both in the content posted to it, and the locations of its deployment. An example of this could have been political organising, particularly around calls for "boycotting, divesting and sanctioning The Cloud Regime" (Counter Cloud Action Day), which were present at the festival and subject to differing levels of censorship (Anti-Colonial Tech Panel), along with the anti-extremism protest that took place metres from the festival venue (Rinke and Steitz). | ||
== Interference == | |||
Within the room these sideBand microcontrollers push up against, make fuzzy, and interrupt conventional networking. Wifi routers have a series of 20MHz channels available across which they can make connections. These can usually be configured to work within a different sector within the range, if needed, to avoid interference. | Within the room these sideBand microcontrollers push up against, make fuzzy, and interrupt conventional networking. Wifi routers have a series of 20MHz channels available across which they can make connections. These can usually be configured to work within a different sector within the range, if needed, to avoid interference. | ||
| Line 121: | Line 130: | ||
This activity of wifi misuse recalls the practices of pirate radio which operates against the legal conditions imposed on the electromagnetic spectrum often broadcast within the same frequencies assigned to other stations. Lower powered, temporary and sometimes portable equipment, means that signal propagation will often be relatively local. The stations can be received by a simple consumer radio receiver. Wifi access points may similarly broadcast to a local area, indiscriminately visible to wifi enabled devices. The devices needed to join are (like the radio receivers) generic and designed to operate with these protocols. | This activity of wifi misuse recalls the practices of pirate radio which operates against the legal conditions imposed on the electromagnetic spectrum often broadcast within the same frequencies assigned to other stations. Lower powered, temporary and sometimes portable equipment, means that signal propagation will often be relatively local. The stations can be received by a simple consumer radio receiver. Wifi access points may similarly broadcast to a local area, indiscriminately visible to wifi enabled devices. The devices needed to join are (like the radio receivers) generic and designed to operate with these protocols. | ||
== Carrier Waves == | |||
If part of our exploration of the ServPub server is understood in relation to conventional methods digital networking, how does it react to the smaller unconventional methods of the nodes. In practice the sideBand nodes produce a friction. To connect to the message board or run other services, means disconnecting from the collective spaces of writing on the ServPub server, and the wider internet. It is a hardware switching that interrupts flow. | If part of our exploration of the ServPub server is understood in relation to conventional methods digital networking, how does it react to the smaller unconventional methods of the nodes. In practice the sideBand nodes produce a friction. To connect to the message board or run other services, means disconnecting from the collective spaces of writing on the ServPub server, and the wider internet. It is a hardware switching that interrupts flow. | ||
| Line 131: | Line 140: | ||
A possible use of this could be to share personal shadow libraries, or create ad-hoc | A possible use of this could be to share personal shadow libraries, or create ad-hoc | ||
local web-rings. Using popular software, such as ''Calibre'' (Goyal) and Visual Studio Code's ''Live Server'' extension makes both of these examples relatively simple. As mentioned earlier in the in the Admission section, this becomes practical in settings where the accessible networks are subject to particular censorship or surveillance. | local web-rings. Using popular software, such as ''Calibre'' (Goyal) and Visual Studio Code's ''Live Server'' (Dey) extension makes both of these examples relatively simple. As mentioned earlier in the in the Admission section, this becomes practical in settings where the accessible networks are subject to particular censorship or surveillance. | ||
The microcontrollers that sideBand uses have found similar uses in various artistic and experimental projects. Philadelphia based artist space, Iffy Books published a zine which, referencing the work of Dennis de Bel and Melissa Merritt details instructions for a ''pocket wifi portal''. The uses suggested by Iffy Books include: | The microcontrollers that sideBand uses have found similar uses in various artistic and experimental projects. Philadelphia based artist space, Iffy Books published a zine which, referencing the work of Dennis de Bel and Melissa Merritt details instructions for a ''pocket wifi portal''. The uses suggested by Iffy Books include: | ||
<blockquote> | <blockquote> | ||
* Share an article/essay/political slogan with anyone who happens to be at the coffee shop. | * Share an article/essay/political slogan with anyone who happens to be at the coffee shop. | ||
* Promote an upcoming event without using social media. | * Promote an upcoming event without using social media. | ||
* Share a poetry anthology with other commuters on your train. | * Share a poetry anthology with other commuters on your train. | ||
* Share maps and information on a hiking trip without cell reception. | * Share maps and information on a hiking trip without cell reception. | ||
* Use several wifi boards to send a message using SSID names alone.</blockquote> | * Use several wifi boards to send a message using SSID names alone. | ||
</blockquote> | |||
These playfully construct a variety of ad-hoc publishing techniques and scenarios, which the zine format also contributes to. | These playfully construct a variety of ad-hoc publishing techniques and scenarios, which the zine format also contributes to. | ||
There is a direct link in the formation of these projects to the practices of router hacking that emerged in 2004, building on the ''OpenWRT'' protocol. This gained prominence with ''PirateBox'' (Darts, Strubel), which was further developed by forked repositories such as ''LibraryBox'' (Griffey), both no longer maintained. Projects such as ''Bibliotecha'' ( | There is a direct link in the formation of these projects to the practices of router hacking that emerged in 2004, building on the ''OpenWRT'' protocol. This gained prominence with ''PirateBox'' (Darts, Strubel), which was further developed by forked repositories such as ''LibraryBox'' (Griffey), both no longer maintained. Projects such as ''Bibliotecha'' (Buzova et al) perform similar functions – that is the sharing of media through offline networks. The specific mode of user participation within such networks is a key aspect of the value of these projects in as the Bibliotecha developers write: | ||
<blockquote>When you’re going parallel/serve locally like an actual physical library, the content comes from a particular context and is served in this context. There is a real purpose to it, it is not just sharing for the sake of sharing. ( | <blockquote>When you’re going parallel/serve locally like an actual physical library, the content comes from a particular context and is served in this context. There is a real purpose to it, it is not just sharing for the sake of sharing. (Laforet et al 44)</blockquote><ref> This is documented in the publication by Constant, “Are You Being Served?” (2014), which followed a 2013 event "dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers".</ref> | ||
Beyond the scope of Wi-Fi, other protocols offer similar potential for experimental networking. To give two examples: Near Field Contact is notable particularly for the fact that the device holding the data is powered by the device receiving the data, through the process of inductance when it receives the radio signal. This results in very constrained data limits, however the devices are now ubiquitous, used extensively in stores to tag items. It is also utilised by smartphones, to perform contactless payments – meaning that these devices can read and write these chips. Secondly, ''LoRa'' (Cycleo, Semtech), which is visibly similar to the sideBand boards (usually utilising the newer ESP chip, ESP32) that is a proprietary technique for long range wifi, often conceived as forming mesh networks that pass data node to node, circumventing big tech and state infrastructures. | Beyond the scope of Wi-Fi, other protocols offer similar potential for experimental networking. To give two examples: ''Near Field Contact'' is notable particularly for the fact that the device holding the data is powered by the device receiving the data, through the process of inductance when it receives the radio signal. This results in very constrained data limits, however the devices are now ubiquitous, used extensively in stores to tag items. It is also utilised by smartphones, to perform contactless payments – meaning that these devices can read and write these chips. Secondly, ''LoRa'' (Cycleo, Semtech), which is visibly similar to the sideBand boards (usually utilising the newer ESP chip, ESP32) that is a proprietary technique for long range wifi, often conceived as forming mesh networks that pass data node to node, circumventing big tech and state infrastructures. | ||
This limited sideBand experiment performed a small intervention that affirmed the practices developed by the ServPub collaborators. It would be interesting to deploy the boards again in other settings, and expose their code to other groups of people and networking devices.. Operating in these ways, and with performative functions the sideBand network follows a Luddite logic of unpicking and the creation of space for refusal. The project includes the active dismissal of certain processes and tools, to open the exploration of other strategies and practices, better suited to commonality or the process of imagining such a thing. It remains open to other channels of data, shadow libraries, local wikis or static sites. It both requires and reaffirms a local presence and intimacy with the infrastructure. | This limited sideBand experiment performed a small intervention that affirmed the practices developed by the ServPub collaborators. It would be interesting to deploy the boards again in other settings, and expose their code to other groups of people and networking devices.. Operating in these ways, and with performative functions the sideBand network follows a Luddite logic of unpicking and the creation of space for refusal. The project includes the active dismissal of certain processes and tools, to open the exploration of other strategies and practices, better suited to commonality or the process of imagining such a thing. It remains open to other channels of data, shadow libraries, local wikis or static sites. It both requires and reaffirms a local presence and intimacy with the infrastructure. | ||
The material conditions of networking infrastructure continue to be a focus within research and arts practices, shaping the development of concepts such as permacomputing, and a wider revival of Luddism. As was clear to the participants of "Are You Being Served?" | The material conditions of networking infrastructure continue to be a focus within research and arts practices, shaping the development of concepts such as permacomputing, and a wider revival of Luddism. As was clear to the participants of "Are You Being Served?", an event dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers: | ||
<blockquote>The necessary infrastructure that is put in place effects our understanding of place, both virtually and physically and it has become increasingly difficult to be intimate with the technologies that we feel familiar with. ( | <blockquote>The necessary infrastructure that is put in place effects our understanding of place, both virtually and physically and it has become increasingly difficult to be intimate with the technologies that we feel familiar with. (Laforet et al 4)</blockquote> | ||
When so much of life is contingent on the so called "connectivity" of the internet and subject to ever greater modes of extraction, a template of autonomous zones and fragmented protocols appears as a necessary practice. The methodologies of feminist servers shared by ServPub and sideBand clearly provide an effective route to gaining this proximity to infrastructure and the tools to shape other forms. | When so much of life is contingent on the so called "connectivity" of the internet and subject to ever greater modes of extraction, a template of autonomous zones and fragmented protocols appears as a necessary practice. The methodologies of feminist servers shared by ServPub and sideBand clearly provide an effective route to gaining this proximity to infrastructure and the tools to shape other forms. | ||
[[File:Image1.png|thumb| | [[File:Image1.png|thumb|400px|Figure 8: Wemos D1 mini underside.]] | ||
[[File:Image2.png|thumb| | [[File:Image2.png|thumb|400px|Figure 9: Wemos D1 mini topside.]] | ||
== Notes == | == Notes == | ||
| Line 171: | Line 183: | ||
== Works cited == | == Works cited == | ||
<div class="workscited"> | |||
Andersen, Christian Ulrik, and Søren Bro Pold. ''The Metainterface''. The MIT Press, 2018. | |||
''Anti-Colonial Tech Panel''. 2024, https://pad.riseup.net/p/r.5e8fb6bd54cdce773db487845244e55d. | ''Anti-Colonial Tech Panel''. 2024, https://pad.riseup.net/p/r.5e8fb6bd54cdce773db487845244e55d. | ||
Arboleda, Martin. ''Planetary Mine | Arboleda, Martin. ''Planetary Mine''. Verso, 2020. | ||
Barragán, Hernando. ''Wiring''. 2003. | Barragán, Hernando. ''Wiring''. 2003. | ||
BBC. "Von Neumann Architecture" | BBC. "Von Neumann Architecture." ''BBC Bitesize''. https://www.bbc.co.uk/bitesize/guides/zhppfcw/revision/3. Accessed 12 Mar. 2024. | ||
Benchoff, Brian. "New Chip Alert: The ESP8266 WiFi Module (It’s $5)" | Benchoff, Brian. "New Chip Alert: The ESP8266 WiFi Module (It’s $5)." ''Hackaday'', 26 Aug. 2014. https://hackaday.com/2014/08/26/new-chip-alert-the-esp8266-wifi-module-its-5/ | ||
Berends, Manetta, and Simon Browne. ''Wiki4print''. 2023. https://wiki4print.servpub.net/index.php?title=Wiki4print. | Berends, Manetta, and Simon Browne. ''Wiki4print''. 2023. https://wiki4print.servpub.net/index.php?title=Wiki4print. | ||
Bez, Roberto, Emilio Camerlenghi, Alberto Modelli, Angelo Visconti. "Introduction to Flash Memory". ''Proceedings of the | Bez, Roberto, Emilio Camerlenghi, Alberto Modelli, Angelo Visconti. "Introduction to Flash Memory". ''Proceedings of the IEEE'', vol. 91, no. 4, Apr. 2003, pp. 489–502. IEEE Xplore, https://doi.org/10.1109/JPROC.2003.811702 | ||
Binfield, Keven. ''Writings of the Luddites''. John Hopkins University Press, 2004. | Binfield, Keven. ''Writings of the Luddites''. John Hopkins University Press, 2004. | ||
Buzova, Yoana, Lasse van den Bosch Christensen, André Castro, Lucia Dossin, Max Dovey, Michaela Lakova, Martino Morandi, Ana Luísa Moura, Lídia Pereira, Roel Roscam Abbing, et al. ''Bibliotecha''. 2013. https://web.archive.org/web/20210927121215/https://bibliotecha.info/ | |||
''Content/Form, A Peer-Reviewed Newspaper,'' vol. 13, no. 1, 2024 | |||
2024, https://darc.au.dk/fileadmin/DARC/newspapers/Content-Form%20A-Peer-Reviewed-Newspaper-Volume-13-Issue-1-2024.pdf | |||
''Counter Cloud Action Day''. 2024, https://www.tecnosandias.org/8m. | ''Counter Cloud Action Day''. 2024, https://www.tecnosandias.org/8m. | ||
Courbon, Franck | Courbon, Franck, Sergei Skorobogatov and Christopher Woods. "Reverse Engineering Flash EEPROM Memories Using Scanning Electron Microscopy". Springer, 2017. https://doi.org/10.17863/CAM.7164. | ||
Darts, David, and Matthias Strubel. ''PirateBox''. 2011, https://piratebox.cc/start. | |||
Dey, Ritwick. ''Live Server''. 2017, https://ritwickdey.github.io/vscode-live-server/. | |||
Dunbar-Hester, Christina. ''Low Power To The People''. The MIT Press, 2014. | Dunbar-Hester, Christina. ''Low Power To The People''. The MIT Press, 2014. | ||
Espressif. ''ESP8266ex Datasheet''. Espressif, 2023. | Espressif. ''ESP8266ex Datasheet''. Espressif, 2023, https://www.espressif.com/sites/default/files/documentation/0a-esp8266ex_datasheet_en.pdf. | ||
''Etherpad''. Etherpad Foundation, 2008. | ''Etherpad''. Etherpad Foundation, 2008, https://etherpad.org. | ||
Feranec, Robert. "How to Make Custom ESP32 Board in 3 Hours". 2023, https://www.youtube.com/watch?v=S_p0YV-JlfU. | Feranec, Robert. "How to Make Custom ESP32 Board in 3 Hours". 2023, https://www.youtube.com/watch?v=S_p0YV-JlfU. | ||
| Line 209: | Line 227: | ||
Flynn, Elizabeth Gurley. Sabotage, The Conscious Withdrawal of the Workers’ Industrial Efficiency. IWW Publishing Bureau, 1916, https://archive.iww.org/history/library/Flynn/Sabotage/. | Flynn, Elizabeth Gurley. Sabotage, The Conscious Withdrawal of the Workers’ Industrial Efficiency. IWW Publishing Bureau, 1916, https://archive.iww.org/history/library/Flynn/Sabotage/. | ||
Fouilloux, Anne. 'Introduction to the Internet of Things (IoT): ESP8266 Architecture and Arduino GUI". | Fouilloux, Anne. 'Introduction to the Internet of Things (IoT): ESP8266 Architecture and Arduino GUI". https://annefou.github.io/IoT_introduction/02-ESP8266/index.html. | ||
Galloway, Alexander R. ''Protocol''. The MIT Press, 2004. | Galloway, Alexander R. ''Protocol''. The MIT Press, 2004. | ||
| Line 215: | Line 233: | ||
Goyal, Kovid. ''Calibre''. 2006, https://calibre-ebook.com. | Goyal, Kovid. ''Calibre''. 2006, https://calibre-ebook.com. | ||
Griffey, Jason. ''LibraryBox''. 2012. | Griffey, Jason. ''LibraryBox''. 2012, https://jasongriffey.net/librarybox/. | ||
Halfacree, Gareth. "Raspberry Pi Confirms a Planned IPO, But Says Hobbyists Will Remain 'Incredibly Important'". ''Hackster.Io'', https://www.hackster.io/news/raspberry-pi-confirms-a-planned-ipo-but-says-hobbyists-will-remain-incredibly-important-f7b9625e0d52. Accessed 8 Mar. 2024. | Halfacree, Gareth. "Raspberry Pi Confirms a Planned IPO, But Says Hobbyists Will Remain 'Incredibly Important'". ''Hackster.Io'', https://www.hackster.io/news/raspberry-pi-confirms-a-planned-ipo-but-says-hobbyists-will-remain-incredibly-important-f7b9625e0d52. Accessed 8 Mar. 2024. | ||
Hay, Douglas, Peter Linebaugh and E. P. Thompson. ''Albion’s Fatal Tree''. Allen Lane, 1975. | |||
''Iffy Books Pocket Wifi Portal Zine''. Iffy Books, 2022, https://iffybooks.net/pocket-wifi-portal. | |||
Illich, Ivan. ''Tools for Conviviality''. Harper & Row, 1973. | Illich, Ivan. ''Tools for Conviviality''. Harper & Row, 1973. | ||
| Line 225: | Line 245: | ||
Ilmer, Veniamin. ''Veniamin-Ilmer/Decoding_rom''. 2024. 6 Mar. 2024. GitHub, [https://github.com/veniamin-ilmer/decoding%20rom https://github.com/veniamin-ilmer/decoding_rom]. | Ilmer, Veniamin. ''Veniamin-Ilmer/Decoding_rom''. 2024. 6 Mar. 2024. GitHub, [https://github.com/veniamin-ilmer/decoding%20rom https://github.com/veniamin-ilmer/decoding_rom]. | ||
Karagianni, Mara. Systerserver Diagram. ''Content/Form, A Peer-Reviewed Newspaper'', 2024. | Karagianni, Mara. "Systerserver Diagram." ''Content/Form, A Peer-Reviewed Newspaper'', vol. 13, no. 1, 2024, p. 1. | ||
Laforet, Anne, Marloes de Valk, Madeleine Aktypi, An Mertens, Femke Snelting, Michaela Lakova, Reni Höfmuller (Eds.). "Are you being served? | Laforet, Anne, Marloes de Valk, Madeleine Aktypi, An Mertens, Femke Snelting, Michaela Lakova, Reni Höfmuller (Eds.). "Are you being served? (notebooks)". Constant, 2014, https://calibre.constantvzw.org/book/17. | ||
LoRa. ''Cycleo''. Semtech, 2014. | LoRa. ''Cycleo''. Semtech, 2014. | ||
| Line 241: | Line 261: | ||
Marriott, Nicholas. ''Tmux''. 2007. | Marriott, Nicholas. ''Tmux''. 2007. | ||
Pattnayak, Tapan, and Guhapriyan Thanikachalam. "Antenna Design and RF Layout Guidelines". ''Infineon Technologies'', 2018, | Pattnayak, Tapan, and Guhapriyan Thanikachalam. "Antenna Design and RF Layout Guidelines". ''Infineon Technologies'', 2018, http://www.cypress.com/go/AN91445 | ||
Reas, Casey, and Ben Fry. ''Processing''. 2001. | Reas, Casey, and Ben Fry. ''Processing''. 2001. | ||
| Line 247: | Line 267: | ||
Rinke, Andreas, and Christoph Steitz. "Around 200,000 Gather across Germany in Latest Protests against Far-Right". ''Reuters'', 3 Feb. 2024. https://www.reuters.com/world/europe/least-120000-gather-berlin-latest-round-protests-against-far-right-2024-02-03/. | Rinke, Andreas, and Christoph Steitz. "Around 200,000 Gather across Germany in Latest Protests against Far-Right". ''Reuters'', 3 Feb. 2024. https://www.reuters.com/world/europe/least-120000-gather-berlin-latest-round-protests-against-far-right-2024-02-03/. | ||
Shaw, Aurynn. "A Case Study on Raspberry Pi's Incident on the Fediverse." ''Eiara Limited - Sustainable DevOps'', https://eiara.nz/posts/2022/Dec/09/a-case-study-on-raspberry-pis-incident-on-the-fediverse/. Accessed 27 Mar. 2024. | |||
Shaw, Aurynn. "A Case Study on Raspberry Pi's Incident on the Fediverse | |||
Sheldon, Robert, and Carol Silwa. "NAND Flash Wear-Out" | Sheldon, Robert, and Carol Silwa. "NAND Flash Wear-Out." ''Tech Target'', https://www.techtarget.com/searchstorage/definition/NAND-flash-wear-out. Accessed 12 Mar. 2024. | ||
Shiffman, Daniel. "Interview with Casey Reas and Ben Fry" | Shiffman, Daniel. "Interview with Casey Reas and Ben Fry." ''Rhizome'', 23 Sept. 2009, https://rhizome.org/editorial/2009/sep/23/interview-with-casey-reas-and-ben-fry/. | ||
Starosielski, Nicole. ''The Undersea Network''. Duke University Press, 2015. | Starosielski, Nicole. ''The Undersea Network''. Duke University Press, 2015. | ||
Sumi, Denise Helene. "Pirate Care and Usable Politics and Pedagogies". | Sumi, Denise Helene. "Pirate Care and Usable Politics and Pedagogies". ''Content/Form, A Peer-Reviewed Newspaper'', vol. 13, no. 1, 2024, p. 13. https://darc.au.dk/fileadmin/DARC/newspapers/Content-Form_A-Peer-Reviewed-Newspaper-Volume-13-Issue-1-2024.pdf | ||
Thacker, Eugene. "Introduction to Protocol" | Thacker, Eugene. "Introduction to Protocol." In Alexander R. Galloway, ''Protocol''. The MIT Press, 2004. | ||
Thompson, E. P | Thompson, E. P. ''The Making of the English Working Class''. Pantheon Books, 1980. | ||
- | Upton, Eben. "Production and Supply-Chain Update". ''Raspberry Pi'', 4 Apr. 2022, https://www.raspberrypi.com/news/production-and-supply-chain-update/. | ||
"What Is Arduino?", ''Arduino,'' 2018, https://www.arduino.cc/en/Guide/Introduction. | |||
</div> | |||
== Biography == | == Biography == | ||
Latest revision as of 12:31, 29 October 2024
Mateus Domingos
Unstable Frequencies
Unstable Frequencies
A Case for Small-scale Wifi Experimentation
Abstract
In this essay I describe an experimental wifi network sideBand which provided access to a simple message-board during the Content/Form workshop, held at Haus der Kulturen der Welt in January 2024, as part of transmediale. This is considered in relation to the collaborative infrastructure ServPub that was carefully assembled and maintained for the workshop. The production of the hardware and software required for the sideBand network is described with specific consideration of the types of memory and data storage systems that are utilised. The programming that provided message-board (and wider) functionality is also described. The conditions of this production along with the specific ways in which use of the network unfolds are considered in relation to Dunbar-Hester’s propagation and a Luddite framing, that includes sabotage and refusal. This is argued as producing other ways of understanding infrastructure and place, related to the feminist methodologies of ServPub.
Introduction
The Content/Form research workshop questioned of the ways in which research practices are "shared and reviewed, and the infrastructures through which [they are] served." Participants gained access to the specially convened ServPub infrastructure, engaging with the self-managed server and the various software and memory systems provided.[1] Inviting space for a parallel imagination of these networks, I used wifi-enabled micro-controllers to introduce offline access points, serving a simple message board (referred to hereafter as sideBand). I argue that this intervention provokes a counter-knowledge of the internet and networking infrastructures. My intention was for sideBand to act as a shadow network to the primary shared space of ServPub, augmenting our interactions with the server and the collective writing processes.
Networked data streams always function through protocological layers which perform different functions that in combination allow communication or transmission. They do so within a chain of binary data operating along a one-dimensional line. As Alexander Galloway describes:
At each phase shift (i.e., the shift from HTML to HTTP, or from HTTP to TCP), one is able to identify a data object from the intersection of two articulated protocols. In fact, since digital information is nothing but an un-differentiated soup of ones and zeros, data objects are nothing but the arbitrary drawing of boundaries that appear at the threshold of two articulated protocols. (Galloway 52)
This nesting of protocols extends to the transport medium, such as "fiber-optic cables, telephone lines, air waves, etc." (Galloway 11) as well as bodies.
As Deleuze shows in the 'Postscript on Control Societies,' protocological control also affects the functioning of bodies within social space and the creation of these bodies into forms of ‘artificial life’ that are dividuated, sampled, and coded. (Galloway 12)
The ServPub infrastructure and feminist technological practices produce a visibility of the nodes of networking infrastructure. This is evidenced particularly in the visual diagramming and open documentation of installation and maintenance processes that accompany the group’s publications, talks and interventions. The sideBand microcontrollers pursue a further visibility through smaller discrete components and selective use of existing infrastructures. The sideband infrastructure is more brittle than the wider network, because in the spirit of permacomputing and visibility, technical capability is traded for limited parameters that surface protocological moments into active decisions. Using this limited reduced component architecture, narrows the scope of this inquiry, as a strategy for gaining some specificity of the various material entanglements. For instance, it becomes somewhat more trivial for someone without formal technical knowledge of computer hardware to learn where the memory is inscribed and under what levels of permanence, and also begin to follow the combination of manufacturers at least partially involved in the assembly of this microcontroller.
Following the naming conventions of the newspaper and wiki4print (Berends, Browne), I’ll use the word editors to refer to users of the wiki4print platform, which includes the workshop participants, organisers and caretakers of the infrastructure.
Mapping
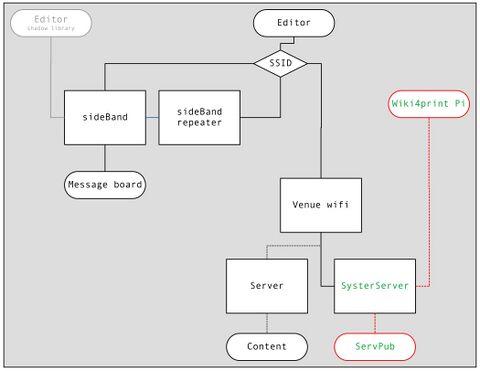
The ServPub infrastructure has been documented in depth by its participants in the newspaper, online, and within this journal. Based on the diagram by Mara Karagianni, I include a brief outline of the structure here in order to contextualise the observations I am drawing. This diagram also shows how the sideBand network occupies space alongside the ServPub network.
The diagram maps the modes of connection to the sideBand network, the ServPub organised wiki4print platform and common retrieval of websites. The editor is imagined as selecting a wifi network or service set identifier (SSID) to join at which point the paths of data diverge. In the organisation of this diagram, blocks closer to the top of the diagram are more likely visible to the editors. This visibility mostly aligns with opportunity for control over those blocks (e.g. through removing the power source).
Our interaction and use of both the sideBand message board and the ServPub wiki as editors are performed within a web browser. With ServPub this included complex software such as Etherpad and the MediaWiki (Crocker, Manske) based wiki4print, described as "not only a repository tool for print, but as something that contributes to a larger whole and network of voices." (Content/Form 1) There is a distinction in the way the platforms are maintained, or that adjustments can be made to their configuration and programming. Within ServPub this will often include the collaborative programming that is done via SSH[2] sessions and the shared command line software tmux (Marriott). The functioning of the device can be rewritten as needed potentially whilst services remain online.
In the sideBand network the access points are limited to the programmed configuration and whatever other affordances may be found in the conventional processes of port forwarding. Re-programming of the sideBand access points is possible (and was encouraged) but would force disconnection and erasure of any active connections.
A key distinction, which situates the following essay, is contained within the first step from editor device to the network. The ServPub setup was joined via the wifi provided by the workshop venue, and as such, not controlled by the participants. As the network included multiple servers in different locations, the data was making long international loops to reach back to the device that was in the room. Conversely the sideBand network was contained within the room, with data passing directly between the sideBand device and the editor device.
Side Bands
This kind of networking performed by the sideBand, could perhaps be described as shadow-networking, borrowing the nomenclature from shadow libraries and the dark web. These practices challenge the permitted use of existing infrastructures. Their operation follows pirate principles (Sumi 13). The uses of sideBand that editors took most interest in was perhaps those that performed as elements of a shadow library structure. I am using the term sideBands to refer more specifically to a technical phenomenon, that relates to the relational quality of the networks.
Side bands are the range of radio frequencies either side of the carrier wave modulated by the transmitted signal. This transmission is mirrored as an upper side band and a lower side band. This occurs within the transmission of both analogue and digital information. Transmitting either one of these frequency bands can allow the signal to be reconstructed by a receiver. Protocols have been developed to exploit this artefact of modulation, and their continued development is of continued interest within amateur radio communities. Within the limited bandwidths available, techniques that produce signals at narrower bandwidth have always been important and novel developments are often made by tinkering amateurs.
Rhyming with the side band phenomenon, the kind of networking explored with the sideBand exists within the affordances of protocol that collectively assemble into a functioning internet. A selective use and adaptation of parts of this framework generate a different system of transmission. It directly utilises a narrowing of frequencies and the ability to re-assemble transmissions. This occurs through the selective use of wifi channels and the local, social structure, or bodies, that are present with the devices.
It is in some respects an inversion of the ServPub model. Instead of creating a communal, distributed infrastructure, a looser proliferation of isolated networks is expected. This inherently limits the scope of the activity whilst surfacing a visibility of components and network paths. The hardware is built from comparatively few components, most of which are clearly visible. This affords an awareness of processes that relates to Christian Ulrik Andersen and Søren Bro Pold's framing of technology critique that combine "semantic processes of signification with machinic processes of signals." (14)
There is also a link here to radio activism, as described by Christina Dunbar-Hester in her account of low power FM radio activism and the Prometheus Radio Project. Dunbar-Hester argues that these radio activists are "'propagators’ of technology."
I use the term propagation specifically to refer to the intertwined practices of discursive and material engagement with an artifact. Propagators shape the form, meaning, and use of a given artifact through argumentation and mediating work to audiences such as users or regulators." (Dunbar-Hester 23)
Propagation, as the phrasing implies a transmission of knowledge, its reception and ongoing transmission. Crucially this includes practical engagements with an artifact that might not produce an improvement or objective change in the functioning of that artifact. Instead, it is the political and social relationships that are felt as important in the act of propagation. Dunbar-Hester describes this through the example of a weekend with activists spent repairing a decommissioned radio transmitter, that was undertaken without a clear use for the transmitter identified and did not fully complete the repairs (69). Much of Dunbar-Hester’s study reflects on the Prometheus organisation’s barnraising events. These large gatherings were the culmination of extensive processes of planning, licence application and fundraising that performed the physical construction of a low powered radio station. The technical processes involved in the construction of the station were often relatively trivial to experienced technicians, however it was important to the activists that the barnraising proceeded in a way facilitated learning, in combination with the logistical and care work that was also essential to the event (20).
My use of the specific sideBand micro-controllers stems from their apparent potential to fulfil this kind of propagation entanglement: their functionality offers a low-code entry into the programming and exploration of networking devices. Given their inherent limitation, they contain a surprising amount of flexibility, leading to interesting experimental use cases. The sideBand nodes suggest an expanded introduction to these techniques.
Following the imagined propagation of these isolated networks, comparisons can be made to the historical resistance of the Luddites. If the aim of these engagements with networking infrastructure include the possibilities of changing them, reorienting them towards more equitable ends, then the template of hardware destruction that the Luddite resistance performed can be instructive.
Luddism in its original guise was resistant to changes rendered in the workplace, often embodied in the deployment of machinery that automated increasing stages of production processes. Its methods of refusal and sabotage attacked these machines, and it is commonplace to articulate a Luddite stance in regard to contemporary technologies, or as certain effects of their use become apparent. Despite its eventual suppression and failures, Luddism suggests techniques for organisation and collective action. The methods of resistance employed and reasons for it were not unique to Luddism, but rather appear as part of a tapestry of woven solidarities and movements that emerged from the specific conditions imposed on the population (Thompson).
Dunbar-Hester is careful to distinguish propagators from 'mere' Luddites (Dunbar-Hester 181). The radio activism she describes emerges more through uses of specific technologies and appeals to legal frameworks than a retreat from legal options and a destruction of machinery. I don’t quite draw such a distinction as the Luddite activities did include attempts at gaining certain protections through charters and the halting destruction of machinery could reflect a radical flank of a wider movement agitating against the imposed conditions (Malm 50).
The sideBand provocation was suggestive of some of the Luddite strategies, if not also performing them in some minor ways. Including, forms of sabotage and refusal. Sabotage – or the withdrawal of efficiency (Flynn), is enacted through occupation of the network spaces with brittle replacements (sideBand micro-controllers). Refusal is understood through the call to "put down all machinery harmful to commonality" (Binfield 57). Recognising implicit harms to commonality in conventional computational technologies and networking infrastructure, the sideBand escapes (or limits exposure to) some aspects of the conventional networking infrastructure (which is essential to larger scale networking) as does Servpub.
Through the limited sideBand nodes, there is a potential that these processes of sabotage and refusal can be negotiated and performed, if only as a limited moment of reflection and critique within the small scale of the workshop. As networking complexity increases, the malleability of the systems for novice programmers is diminished. This isn't intended to argue for non-complexity in the infrastructures we attempt to build as communities. It is instead about a parallel point of access that supports propagation and provides waypoints to complexity.
Components
The ServPub network operated across a range of machines. Centrally it was using multiple Raspberry Pi's. In the same way that all commercially available computer systems should be challenged regarding their ecological impacts and ethical implications (Arboleda; Kara; Starosielski), the Raspberry Pi can be seen as a troubling device for communities engaged with anti-colonial and feminist protest.
Despite the apparently democratising potential of Raspberry Pi at its outset, the egalitarian potential has not been fulfilled. Although it remains relatively cheap and benefits from established documentation and experimentation; a planned Initial Public Offering (Halfacree), fraught social media engagement (Shaw), and a frequent lack of availability to hobbyists as stock is bought up by industrial firms (Upton), all introduce questions about the suitability of the system. The sideBand uses devices that are no less valid as targets for scrutiny and questioning as to their suitability. They exist however, within a different set of conditions that seem to both reveal and hide various elements of their manufacture to different degrees.
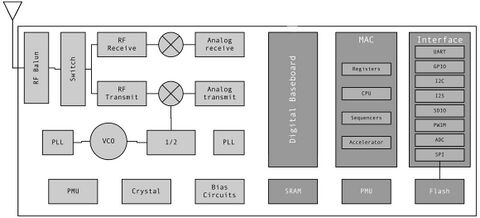
The ESP8266 is produced by Chinese semiconductor firm, Espressif. They describe themselves as a world leading AIoT (Artificial Intelligence of Things) company and by late 2023 they had shipped over 1 billion chips (Espressif). They are well known for their ESP range of chips which feature networking components such as wifi. Their devices are designed to work with Espressif's own open-source SDKs as well as other alternatives, such as Arduino. As with Raspberry Pi, they are designed primarily for industrial use. The ESP chips have also been developed into so-called development boards. This places the chip within a printed circuit board that contains the necessary components to enable simple programming and operation, allowing inputs/outputs and USB connection. The model I am using is the D1 Mini, originally designed by Lolin (based on a module by Ai-Thinker). As they became available in these hobbyist-friendly forms they were quickly adopted as a flexible part of IoT (Internet of Things) tinkering, despite initially having no English documentation (Benchoff).
The D1 Mini contains a handful of visible components. The antenna is a copper trace etched onto the board like a strange glyph. The intended use of the board is signed and performed by this as the length of the trace corresponds to antenna theory and is (with an adjustment for impedance) a quarter wavelength long (Pattnayak, Thanikachalam 4). Because the hardware is open sourced it allows hobbyists to experiment with the construction of these boards. This structure means that it is possible for hobbyists to design their own versions of these development boards and have them manufactured with relative ease (Feranec). This means that there are also many different companies producing these development boards, and that they continue to be readily available despite their limitations and superior later models.
To program the board I have been using Arduino, "an open-source electronics platform based on easy-to-use hardware and software." ("What Is Arduino?") It is a popular choice for hobbyists to experiment with electronics, often utilising sensors and other components. The integrated development environment (IDE) shares a lineage with experimental artistic coding as it built on Wiring (Barragán) which the creators of Processing, Casey Reas and Ben Fry describe as "an electronics version of Processing that used our programming environment and was patterned after the Processing syntax" (Shiffman). It's relevant to note as well, that Reas and Fry also express their excitement at the "iteration and growth of this community" and cite the earlier software and projects that informed Processing.
Message Board
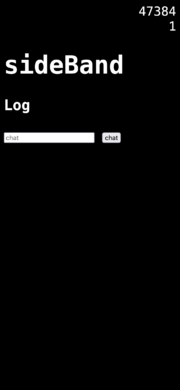
The sideBand locally hosts a simple message board website. It is a small page of HTML that assembles itself each time it is requested, to include any new data submitted by the editors. It makes use of a handful of basic HTML elements with styling performed inline. The more complex element is the form, which provides the functionality for editors to post messages. The messages are stored as variables that pass through the Arduino code and are able to act in parts of the program other than the displayed HTML. Despite being messy and inefficient, the code for this program is quite accessible for editors with little coding experience. Much of the functionality of the sideBand server is contained and performed within libraries that are part of the IDE. In the process of programming, we can call on these libraries and use certain functions with the expectation that they will continue to perform expected tasks (such as handle new editors joining the SSID).
Foregoing some of the checks that might be made as standard practice if deploying a form online primarily to avoid code injection attacks, minimal checks are here performed on the validity of submitted data. This introduces an unstable zone, where editors have increased agency over the functionality of the message board. They could, for example, submit HTML markup to alter the display of the posts. This is also a vector through which the editors could disable the board if they chose to. This brittle state can be both useful and limiting.
Memories
When using computers, we are interacting with machines that manipulate data and instructions following established architectures, with differing affordances. These machines are usually based on the Von Neumann architecture, in which the "data and instructions are both stored in primary storage" (BBC). An alternative to this is the Harvard architecture, meaning that data and instructions are stored separately. This architecture remains common in microcontrollers where the limited instruction and data memory make it suitable (Fouilloux). This provides an interesting point of difference in the fundamental interaction with these devices and general processes of computation.
The sideBand program stores variables in static random-access memory (SRAM). This is a volatile method of data storage, which means that when it loses power the data is lost. Conversely, flash memory is used to store the program information. This is a non-volatile method of data storage, with permanence, whether or not the device is powered. However, it is still vulnerable to damage, and the processes of re-writing or re-flashing the memory will cause failure after a number of cycles (often estimated at 10000). This is because, with each re-write there is a physical degradation of the oxide layer which prevents the controlled manipulation of the electrons (Bez et al; Sheldon, Silwa). Flash memory itself is organised along principles that are familiar to modes of publishing. It is arranged physically as stacks of pages, laid out in grids that look like the galleys of a book. This works metaphorically through diagrammed understanding of the board (fig. 7) and as a potential act of reading. Given this material configuration it would actually be possible to read the code visually using advanced microscopy techniques (Courbon, Skorobogatov, Woods).[3]
Accessing the sideBand network would in most cases force a user to disconnect from other networks since the usual operation of phones or laptops only allows for a connection to one wifi network at a time to avoid routing conflicts. On some devices this process prompts a warning to the editor that they will not be able to connect to the internet. In the process of connecting to a new network some devices will try to ping a service, in order to receive a response confirming they are online. The response generated when connected to the sideBand network is unsuccessful and so triggers the warning. The device presents this as something you shouldn't do and circumventing it usually takes a few more steps to assure the device that you do wish to connect to this offline network. This hints at the levels of invisible communication our devices have with centralised platforms throughout their use.
If the sideBand microcontroller is reset or encounters an error, the data posted to the message log is not saved. Drawing on Eugene Thacker's assertion that "the moment of disconnectivity is the moment when protocol most forcefully displays its political character" (Thacker xvi) we can identify this as a crucial part in our understanding of the political possibilities that the sideBand represents. The use of the network is collectively understood to be temporary and subject to either chance failure or forced failure (as through code injection, or switching off the power supply). This necessarily shapes what a community might decide to share there or not. Methods of saving the log could also be enacted if the editors wished. Once the page has loaded to their device they could save the page locally or make screenshots at any time.
Increasing usage of the sideBand also increases the likelihood of it failing. The code was written in such a way that it would soon reach the limits of its memory and require resetting. This was indicated in the website interface with a counter that showed current available memory. The sideBand is brittle and limited. For any sustained use it requires a careful, deliberate kind of engagement; with an expanded possibility to slow, pause or preserve the data that emerges.
Admission
The use of the sideBand starts from a collective expectation of its limits as described above. It is important that they were introduced to the group in this way to be clear in the way that the network was lacking features that might be expected. Admission to the space requires knowledge to be shared between peers. In this sharing of the password the group of editors becomes possible. Bypassing a usual layer of internet browsing, the message board website is reached at an IP address instead of a domain name.
Beyond the option of removing the sideBand power supply there are no moderation tools or policies enforced by the software. The acceptable behaviours of a group of people working together, with computers that might usually be ceded to established hardware and software limitations or a coded range of possibilities remain negotiable using other channels within the room, such as voice, a handwritten note, or list of rules taped to a wall.
This process of admission and group formation echoes the use of oaths and passwords within many organisations, covert or not. The Luddites, for example, called the initiation of the oath, "the tying in". It was deemed at that time a transgressive act, and punishable by execution or transportation (Ludd). These processes of course rely on the bonds of trust and honesty between the participants, and produce an interdependence For the Luddites this was frequently undermined by the infiltration of government spies. The uses of the sideBand described here do not necessarily produce outcomes that require careful sensitivity as to the process of admission. However, it does form a space that is potentially subject to legal ramifications both in the content posted to it, and the locations of its deployment. An example of this could have been political organising, particularly around calls for "boycotting, divesting and sanctioning The Cloud Regime" (Counter Cloud Action Day), which were present at the festival and subject to differing levels of censorship (Anti-Colonial Tech Panel), along with the anti-extremism protest that took place metres from the festival venue (Rinke and Steitz).
Interference
Within the room these sideBand microcontrollers push up against, make fuzzy, and interrupt conventional networking. Wifi routers have a series of 20MHz channels available across which they can make connections. These can usually be configured to work within a different sector within the range, if needed, to avoid interference.
During the workshop, with many devices in the room there was no noticeable disruption caused by the sideBand nodes and channel switching or crowding wasn't explored. In programming the sideBand nodes it was necessary to make active decisions and predictions about the potential outcomes, through the channel settings. This draws attention to the possibility of interference that occurs in the physical operation of the devices. Qualities of the network usually assumed to be ephemeral are brought into question and consideration.
A more noticeable interference caused by sideBand was the momentary movement of collective writing from the Etherpad to the sideBand message board. The Etherpad setup was already providing an engaging place for the collaborative note-taking of our individual presentations to develop. This kind of writing often develops its own etiquette and styles based on the participation of the group. To investigate the message board, the Etherpad space had to be temporarily left, leaving a gap in the recorded notes.
This activity of wifi misuse recalls the practices of pirate radio which operates against the legal conditions imposed on the electromagnetic spectrum often broadcast within the same frequencies assigned to other stations. Lower powered, temporary and sometimes portable equipment, means that signal propagation will often be relatively local. The stations can be received by a simple consumer radio receiver. Wifi access points may similarly broadcast to a local area, indiscriminately visible to wifi enabled devices. The devices needed to join are (like the radio receivers) generic and designed to operate with these protocols.
Carrier Waves
If part of our exploration of the ServPub server is understood in relation to conventional methods digital networking, how does it react to the smaller unconventional methods of the nodes. In practice the sideBand nodes produce a friction. To connect to the message board or run other services, means disconnecting from the collective spaces of writing on the ServPub server, and the wider internet. It is a hardware switching that interrupts flow.
The convivial group editing of the wiki, kept the process generously open up to the point when the files needed for printing the newspaper iteration of the journal, the key outcome from the workshop, were generated in the form of a pdf. This is an iterative encapsulation that can be run multiple times. The point is that it does reach a stasis, something objective, that allows it to travel outside of the workshop - to produce research. Counter to this the sideBand produces a timeline of comments, shared within a small range, only until the moment of disconnection.
Dunbar-Hester describes the propagators of Prometheus Radio Project considering the use of wifi and webcasting. Whilst the use of webcasting technologies was deemed mostly not as providing “an equivalent alternative to FM” (164), the possibility of community wifi networks was pursued. This included events similar to the construction of low powered radio stations, but towards the construction of community owned wifi networks. Essential to this process, and a source of contention with other organisations was the Prometheus Radio Project's need for such installations to "lead to a more egalitarian distribution of expertise" (178) in the same way that their work with radio did. The control of infrastructure that a wifi network might produce within a community, and the potential for "networks as platforms for community media rather than Internet connectivity" (181) clearly aligns, for these activists, with the production of radio stations that respond to local conditions and needs.
The sideBand node can also act as a platform for community media. This is a condition inherent in the way routers follow protocological standards. The functionality this provides might be familiar to anyone who has configured a LAN party, set up home automation devices or attempted to wrangle printer software. In public/professional settings there might be additional port settings that interrupt complicate matters, and local device firewall settings can also add wrinkles.
A possible use of this could be to share personal shadow libraries, or create ad-hoc local web-rings. Using popular software, such as Calibre (Goyal) and Visual Studio Code's Live Server (Dey) extension makes both of these examples relatively simple. As mentioned earlier in the in the Admission section, this becomes practical in settings where the accessible networks are subject to particular censorship or surveillance.
The microcontrollers that sideBand uses have found similar uses in various artistic and experimental projects. Philadelphia based artist space, Iffy Books published a zine which, referencing the work of Dennis de Bel and Melissa Merritt details instructions for a pocket wifi portal. The uses suggested by Iffy Books include:
- Share an article/essay/political slogan with anyone who happens to be at the coffee shop.
- Promote an upcoming event without using social media.
- Share a poetry anthology with other commuters on your train.
- Share maps and information on a hiking trip without cell reception.
- Use several wifi boards to send a message using SSID names alone.
These playfully construct a variety of ad-hoc publishing techniques and scenarios, which the zine format also contributes to.
There is a direct link in the formation of these projects to the practices of router hacking that emerged in 2004, building on the OpenWRT protocol. This gained prominence with PirateBox (Darts, Strubel), which was further developed by forked repositories such as LibraryBox (Griffey), both no longer maintained. Projects such as Bibliotecha (Buzova et al) perform similar functions – that is the sharing of media through offline networks. The specific mode of user participation within such networks is a key aspect of the value of these projects in as the Bibliotecha developers write:
When you’re going parallel/serve locally like an actual physical library, the content comes from a particular context and is served in this context. There is a real purpose to it, it is not just sharing for the sake of sharing. (Laforet et al 44)
Beyond the scope of Wi-Fi, other protocols offer similar potential for experimental networking. To give two examples: Near Field Contact is notable particularly for the fact that the device holding the data is powered by the device receiving the data, through the process of inductance when it receives the radio signal. This results in very constrained data limits, however the devices are now ubiquitous, used extensively in stores to tag items. It is also utilised by smartphones, to perform contactless payments – meaning that these devices can read and write these chips. Secondly, LoRa (Cycleo, Semtech), which is visibly similar to the sideBand boards (usually utilising the newer ESP chip, ESP32) that is a proprietary technique for long range wifi, often conceived as forming mesh networks that pass data node to node, circumventing big tech and state infrastructures.
This limited sideBand experiment performed a small intervention that affirmed the practices developed by the ServPub collaborators. It would be interesting to deploy the boards again in other settings, and expose their code to other groups of people and networking devices.. Operating in these ways, and with performative functions the sideBand network follows a Luddite logic of unpicking and the creation of space for refusal. The project includes the active dismissal of certain processes and tools, to open the exploration of other strategies and practices, better suited to commonality or the process of imagining such a thing. It remains open to other channels of data, shadow libraries, local wikis or static sites. It both requires and reaffirms a local presence and intimacy with the infrastructure.
The material conditions of networking infrastructure continue to be a focus within research and arts practices, shaping the development of concepts such as permacomputing, and a wider revival of Luddism. As was clear to the participants of "Are You Being Served?", an event dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers:
The necessary infrastructure that is put in place effects our understanding of place, both virtually and physically and it has become increasingly difficult to be intimate with the technologies that we feel familiar with. (Laforet et al 4)
When so much of life is contingent on the so called "connectivity" of the internet and subject to ever greater modes of extraction, a template of autonomous zones and fragmented protocols appears as a necessary practice. The methodologies of feminist servers shared by ServPub and sideBand clearly provide an effective route to gaining this proximity to infrastructure and the tools to shape other forms.
Notes
- ↑ ServPub is inclusive of hardware, software and the broad constellation of people engaged in this careful practice. It is a collective of collectives, comprised of SysterServer, In-grid, Creative Crowd/Varia, Centre for the Study of the Networked Image at London South Bank University, UCL Slade Schoool of Art, and SHAPE at Aarhus University.
- ↑ Another protocol, Secure Shell (SSH) allows commands to be sent securely between computers across an unsecured network.
- ↑ The process of deciphering programming from photography of chips is commonly part of reverse-engineering efforts aimed at proprietary and/or old hardware (Ilmer; Shirriff).
- ↑ This is documented in the publication by Constant, “Are You Being Served?” (2014), which followed a 2013 event "dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers".
Works cited
Andersen, Christian Ulrik, and Søren Bro Pold. The Metainterface. The MIT Press, 2018.
Anti-Colonial Tech Panel. 2024, https://pad.riseup.net/p/r.5e8fb6bd54cdce773db487845244e55d.
Arboleda, Martin. Planetary Mine. Verso, 2020.
Barragán, Hernando. Wiring. 2003.
BBC. "Von Neumann Architecture." BBC Bitesize. https://www.bbc.co.uk/bitesize/guides/zhppfcw/revision/3. Accessed 12 Mar. 2024.
Benchoff, Brian. "New Chip Alert: The ESP8266 WiFi Module (It’s $5)." Hackaday, 26 Aug. 2014. https://hackaday.com/2014/08/26/new-chip-alert-the-esp8266-wifi-module-its-5/
Berends, Manetta, and Simon Browne. Wiki4print. 2023. https://wiki4print.servpub.net/index.php?title=Wiki4print.
Bez, Roberto, Emilio Camerlenghi, Alberto Modelli, Angelo Visconti. "Introduction to Flash Memory". Proceedings of the IEEE, vol. 91, no. 4, Apr. 2003, pp. 489–502. IEEE Xplore, https://doi.org/10.1109/JPROC.2003.811702
Binfield, Keven. Writings of the Luddites. John Hopkins University Press, 2004.
Buzova, Yoana, Lasse van den Bosch Christensen, André Castro, Lucia Dossin, Max Dovey, Michaela Lakova, Martino Morandi, Ana Luísa Moura, Lídia Pereira, Roel Roscam Abbing, et al. Bibliotecha. 2013. https://web.archive.org/web/20210927121215/https://bibliotecha.info/
Content/Form, A Peer-Reviewed Newspaper, vol. 13, no. 1, 2024 2024, https://darc.au.dk/fileadmin/DARC/newspapers/Content-Form%20A-Peer-Reviewed-Newspaper-Volume-13-Issue-1-2024.pdf
Counter Cloud Action Day. 2024, https://www.tecnosandias.org/8m.
Courbon, Franck, Sergei Skorobogatov and Christopher Woods. "Reverse Engineering Flash EEPROM Memories Using Scanning Electron Microscopy". Springer, 2017. https://doi.org/10.17863/CAM.7164.
Darts, David, and Matthias Strubel. PirateBox. 2011, https://piratebox.cc/start.
Dey, Ritwick. Live Server. 2017, https://ritwickdey.github.io/vscode-live-server/.
Dunbar-Hester, Christina. Low Power To The People. The MIT Press, 2014.
Espressif. ESP8266ex Datasheet. Espressif, 2023, https://www.espressif.com/sites/default/files/documentation/0a-esp8266ex_datasheet_en.pdf.
Etherpad. Etherpad Foundation, 2008, https://etherpad.org.
Feranec, Robert. "How to Make Custom ESP32 Board in 3 Hours". 2023, https://www.youtube.com/watch?v=S_p0YV-JlfU.
Flynn, Elizabeth Gurley. Sabotage, The Conscious Withdrawal of the Workers’ Industrial Efficiency. IWW Publishing Bureau, 1916, https://archive.iww.org/history/library/Flynn/Sabotage/.
Fouilloux, Anne. 'Introduction to the Internet of Things (IoT): ESP8266 Architecture and Arduino GUI". https://annefou.github.io/IoT_introduction/02-ESP8266/index.html.
Galloway, Alexander R. Protocol. The MIT Press, 2004.
Goyal, Kovid. Calibre. 2006, https://calibre-ebook.com.
Griffey, Jason. LibraryBox. 2012, https://jasongriffey.net/librarybox/.
Halfacree, Gareth. "Raspberry Pi Confirms a Planned IPO, But Says Hobbyists Will Remain 'Incredibly Important'". Hackster.Io, https://www.hackster.io/news/raspberry-pi-confirms-a-planned-ipo-but-says-hobbyists-will-remain-incredibly-important-f7b9625e0d52. Accessed 8 Mar. 2024.
Hay, Douglas, Peter Linebaugh and E. P. Thompson. Albion’s Fatal Tree. Allen Lane, 1975.
Iffy Books Pocket Wifi Portal Zine. Iffy Books, 2022, https://iffybooks.net/pocket-wifi-portal.
Illich, Ivan. Tools for Conviviality. Harper & Row, 1973.
Ilmer, Veniamin. Veniamin-Ilmer/Decoding_rom. 2024. 6 Mar. 2024. GitHub, https://github.com/veniamin-ilmer/decoding_rom.
Karagianni, Mara. "Systerserver Diagram." Content/Form, A Peer-Reviewed Newspaper, vol. 13, no. 1, 2024, p. 1.
Laforet, Anne, Marloes de Valk, Madeleine Aktypi, An Mertens, Femke Snelting, Michaela Lakova, Reni Höfmuller (Eds.). "Are you being served? (notebooks)". Constant, 2014, https://calibre.constantvzw.org/book/17.
LoRa. Cycleo. Semtech, 2014.
Ludd, Ned. "Luddite Bicentenary: 12th January 1813: Baron Thomson Passes Sentence on the Convicted Luddites". Luddite Bicentenary, 12 Jan. 2013, https://ludditebicentenary.blogspot.com/2013/01/12th-january-1813-baron-thomson-passes.html.
Kara, Siddharth. Cobalt Red. St Martins Press, 2022.
Malm, Andreas. How to Blow Up a Pipeline. Verso, 2021.
Manske, Magnus, and Lee Daniel Crocker. MediaWiki. Wikimedia Foundation, 2002.
Marriott, Nicholas. Tmux. 2007.
Pattnayak, Tapan, and Guhapriyan Thanikachalam. "Antenna Design and RF Layout Guidelines". Infineon Technologies, 2018, http://www.cypress.com/go/AN91445
Reas, Casey, and Ben Fry. Processing. 2001.
Rinke, Andreas, and Christoph Steitz. "Around 200,000 Gather across Germany in Latest Protests against Far-Right". Reuters, 3 Feb. 2024. https://www.reuters.com/world/europe/least-120000-gather-berlin-latest-round-protests-against-far-right-2024-02-03/.
Shaw, Aurynn. "A Case Study on Raspberry Pi's Incident on the Fediverse." Eiara Limited - Sustainable DevOps, https://eiara.nz/posts/2022/Dec/09/a-case-study-on-raspberry-pis-incident-on-the-fediverse/. Accessed 27 Mar. 2024.
Sheldon, Robert, and Carol Silwa. "NAND Flash Wear-Out." Tech Target, https://www.techtarget.com/searchstorage/definition/NAND-flash-wear-out. Accessed 12 Mar. 2024.
Shiffman, Daniel. "Interview with Casey Reas and Ben Fry." Rhizome, 23 Sept. 2009, https://rhizome.org/editorial/2009/sep/23/interview-with-casey-reas-and-ben-fry/.
Starosielski, Nicole. The Undersea Network. Duke University Press, 2015.
Sumi, Denise Helene. "Pirate Care and Usable Politics and Pedagogies". Content/Form, A Peer-Reviewed Newspaper, vol. 13, no. 1, 2024, p. 13. https://darc.au.dk/fileadmin/DARC/newspapers/Content-Form_A-Peer-Reviewed-Newspaper-Volume-13-Issue-1-2024.pdf
Thacker, Eugene. "Introduction to Protocol." In Alexander R. Galloway, Protocol. The MIT Press, 2004.
Thompson, E. P. The Making of the English Working Class. Pantheon Books, 1980.
Upton, Eben. "Production and Supply-Chain Update". Raspberry Pi, 4 Apr. 2022, https://www.raspberrypi.com/news/production-and-supply-chain-update/.
"What Is Arduino?", Arduino, 2018, https://www.arduino.cc/en/Guide/Introduction.
Biography
Mateus Domingos is a PhD student at the Centre for the Study of the Networked Image, London South Bank University. His research explores the history of the Luddites and the computational technologies used within activist arts practices today. He is based in Leicester, where he works as an art technician and is a member of artist-run Two Queens. ORCID id: 0009-0001-1268-189X